Have you ever received a suspicious email?
Email phishing is a cunning trick cybercriminals use to steal your personal information, and it’s becoming increasingly common.
What’s worse, these scams are not always obvious. They can look like regular emails and might even seem to come from someone you know. It can feel like walking through a minefield every time you check your inbox.
Don’t worry, though, as I’ve got a solution for you.
Our easy-to-understand guide will teach you how to read email headers and identify these phishing scams. Let’s get started –
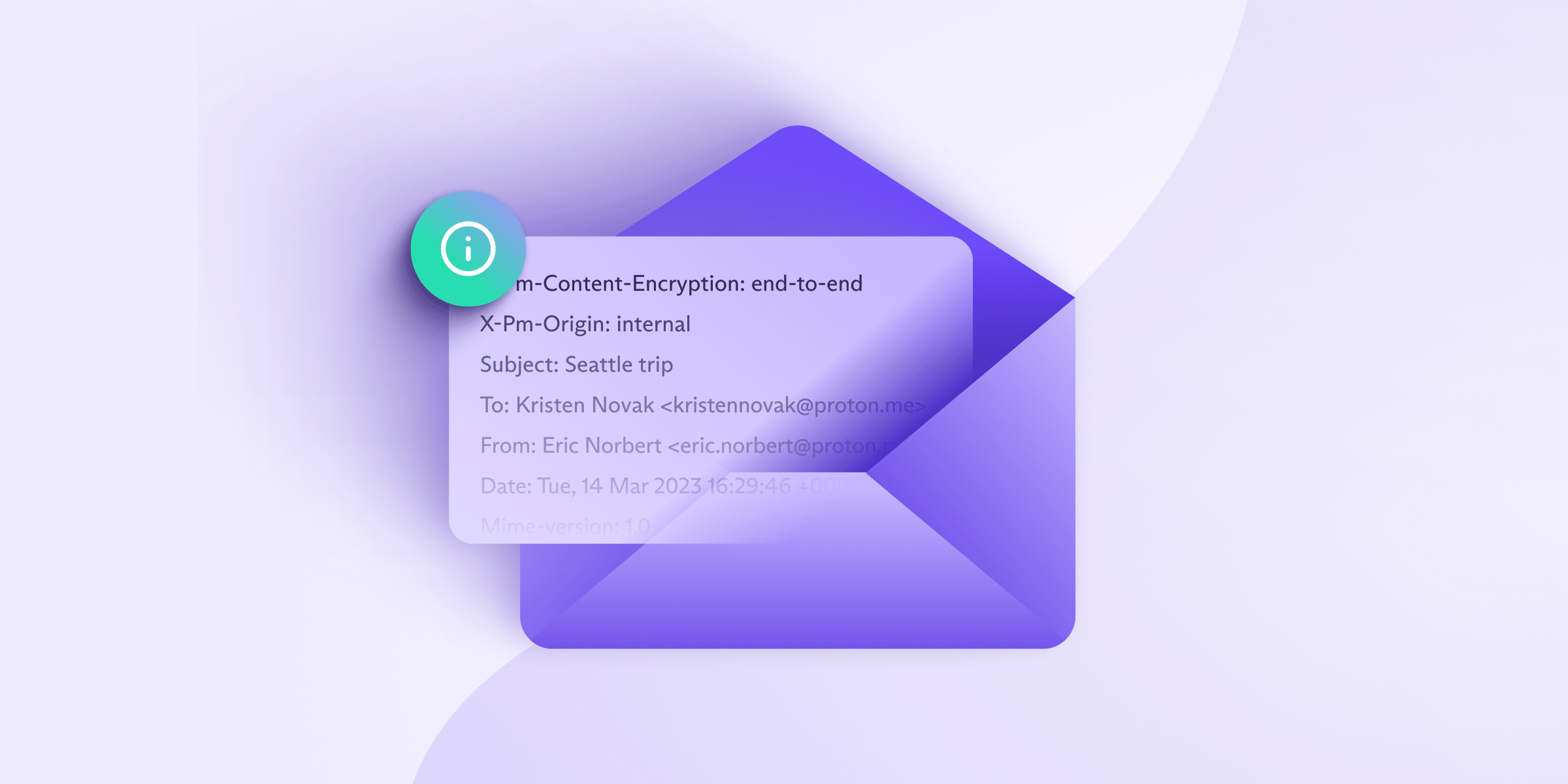
What is an Email Header?
An email header is a section of data associated with an email message containing details about the sender, the recipient, the email’s route to the inbox, and various authentication details. Essentially, it is the digital equivalent of an envelope’s printed information for a snail mail.
Every time a message is sent, the email system automatically attaches this block of technical data at the beginning of the email.
It represents a response trail maintained by all the servers or computers that handle the email from source to destination.
The email header includes several components that give vital information about the email:
- From: This shows who sent the email.
- To: This shows the recipient’s email address(es).
- Subject: It shows the subject of the email.
- Date: When the email was sent.
- Received: Time and date at each point during transmission from the sender to the recipient.
- Return-Path: Address where bounce-backs are delivered if the email can’t be delivered.
- Message ID: A unique identification given to each message.
- X-Spam-Score: Calculated score that determines whether an email is spam.
While the primary headers (From, To, Date, and Subject) are easy to see, the rest of the header information can be found by choosing to view the “original message” or “source” options.
Knowing how to interpret this information can help identify phishing attempts or other suspicious emails, aiding efforts toward better personal and organizational cybersecurity.
How to Access Email Headers in Gmail?
In Gmail, the process to access email headers is straightforward. Here are the step-by-step instructions:
- Open the email: First, find and open the email you want to analyze.
- Click on the vertical ellipsis: Inside the email, in the top right corner, you’ll find a vertical ellipsis (…) or ‘More’ button, depending on your Gmail settings. Click on this button.
- Choose ‘Show original’: In the drop-down menu that appears, select the ‘Show original’ option.
- View the headers: A new tab will open in your browser, displaying the complete email header information. This contains all the technical details about the email, such as the sender, recipient, the servers it passed through, and more.
Remember, email headers might seem confusing due to their technical nature.
However, understanding even a few key components can help uncover useful information about incoming email’s origin and path, which is critical in identifying potential phishing emails.
How to Spot Phishing Using Email Headers?
Identifying phishing attempts involves checking several components within an email header.
Here are some steps you can follow to spot potential phishing attempts:
- Verification checks failure: Email systems usually perform various checks to verify the sender’s domain’s legitimacy. If these checks fail, it can indicate a phishing attempt. These checks include SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance).
- Mismatched sender addresses or domains: Sometimes, the sender’s visible name doesn’t match the email address, or the displayed domain doesn’t match the authentic domains of respective organizations, suggesting a phishing email.
- Review the ‘Received’ field: This field tracks the email’s path from sender to receiver. If the path or the servers listed seem unfamiliar, take caution.
- Assess email content: Phishing emails often contain attachments or links that may lead to malicious websites or pose a sense of urgency, requesting immediate action. Also, phishing attempts may contain typos or be poorly written.
- Recheck with sender: If an email was received and there is suspicion around authenticity, even if supposedly from a known person or organization, verify by contacting the sender through separate established communication channels.
By paying close attention to these details in the email headers, you can enhance your ability to identify and avoid falling victim to phishing scams.
How to Check Email Headers for Spoofing?

To check email headers for spoofing, you can analyze various parts of the header to identify inconsistencies or suspicious elements. Follow these steps to examine the headers for spoofing:
- Review the ‘From’ and ‘Return-Path’ fields: Examine the ‘From’ field for any mismatch in the sender’s name and email address or check if the displayed domain doesn’t match the authentic domains of respective organizations. Also, for discrepancies, compare the ‘From’ address with the ‘Return-Path’ address.
- Inspect the ‘Received’ field: The ‘Received’ field of the email header contains the email path from the sender’s server to the receiver’s server. Look for unfamiliar servers in the transmission path or any inconsistencies in the originating server’s domain names.
- Analyze the ‘Message-ID’ field: The ‘Message-ID’ is a unique identifier assigned to each email. If the ‘Message-ID’ domain part doesn’t align with the sender’s domain, it could be a sign of spoofing.
- Check for failed email authentication: Look for indications that SPF, DKIM, or DMARC checks have failed in the email header. These checks are designed to verify the legitimacy of the sender’s domain. Still, spoofed emails may show failure in these authentication methods.
As a general practice, also assess email content for suspicious elements like urgency, poorly written content, or unsolicited attachments and links.
When in doubt, verify the email’s authenticity by contacting the sender through established communication channels.
Common Red Flags in Email Headers
Email headers contain valuable information about the sender, recipient, and path an email has taken.
Analyzing email headers can help identify potential phishing scams, malware deliveries, and other email threats.
Here are some common red flags to look out for:

Mismatched Sender Address
When the sender’s address domain doesn’t match the organization they claim to represent or the email address is misspelled, it may be a phishing attempt.
Fake Display Name
Scammers often use a forged “From” display name to deceive recipients, even if the underlying email address doesn’t match the displayed name.
Unusual Return-Path or Reply-To Addresses
A suspicious email may have a different return path or reply-to address than the sender’s, which can be an attempt to mislead the recipient and avoid detection.
Multiple Recipients or Blind Carbon Copy (BCC)
Messages sent to many recipients or using BCC may indicate spam or phishing attempts.
Unsolicited Attachments
Be cautious of emails with attachments from unknown senders, as they may contain malware or phishing content.
Unexpected Subject Lines
Phishing emails often use urgent or alarming subject lines to create a sense of urgency and trick recipients into taking immediate action.
Shortened or Obfuscated URLs
Scammers may use URL shorteners or obfuscate links to hide the true destination of a link, which can lead to malicious websites.
Missing or Incorrect Message-ID
A missing or incorrect message ID in the email header can signify a spoofed or altered email.
Suspicious X-Mailer/X-Originating-IP
If the X-Mailer or X-Originating-IP header includes an unexpected or suspicious entry, it could indicate that the email is not legitimate.
Excessive Received Headers
Many received headers could signal email routing through multiple servers to obfuscate the sender’s origin.
Understanding these red flags, you can better identify and avoid email threats, keeping your personal information and network secure.
Always exercise caution when opening emails from unknown senders and verify the authenticity of any links or attachments before accessing them.
Final Thoughts
Phishing scams may appear smart and tough to crack, but so are you!
You’ve now learned to read email headers to identify these deceitful attempts and protect your personal information.
And don’t forget, sharing is caring. Teach your friends how to detect phishing scams, too.